A brave warrior stands in front of the harshest enemy, a untouchable evil spirit who possesses his allies. Will they be able to overcome this enemy?
Category: reversing
Solver: 3mb0, HTTP418, mp455
Flag: HTB{Retr0_Kunai}
Writeup
We found ourself here in a reversing challenge. So - as we were used to - we prepare for a static binary analysis. Open Ghidra and install the GhidraBoy [1] to inspect the Game Boy ROM.
We searched around tried to find some sense in the functionalities. But where we suspected the main functionality, we found only a mysterious reference.
So let’s switch the approach. We researched about game boy rom reverse engineering and found the turing agent [2]. This was a quite similar ctf challenge in that the user was also blocked in front of a door.
Here we found a reference to BGB [3] - a GameBoy emulator and debugger. As we wanted to know where the initialization ends and the game logic loop starts, we start playing around with the debugger.
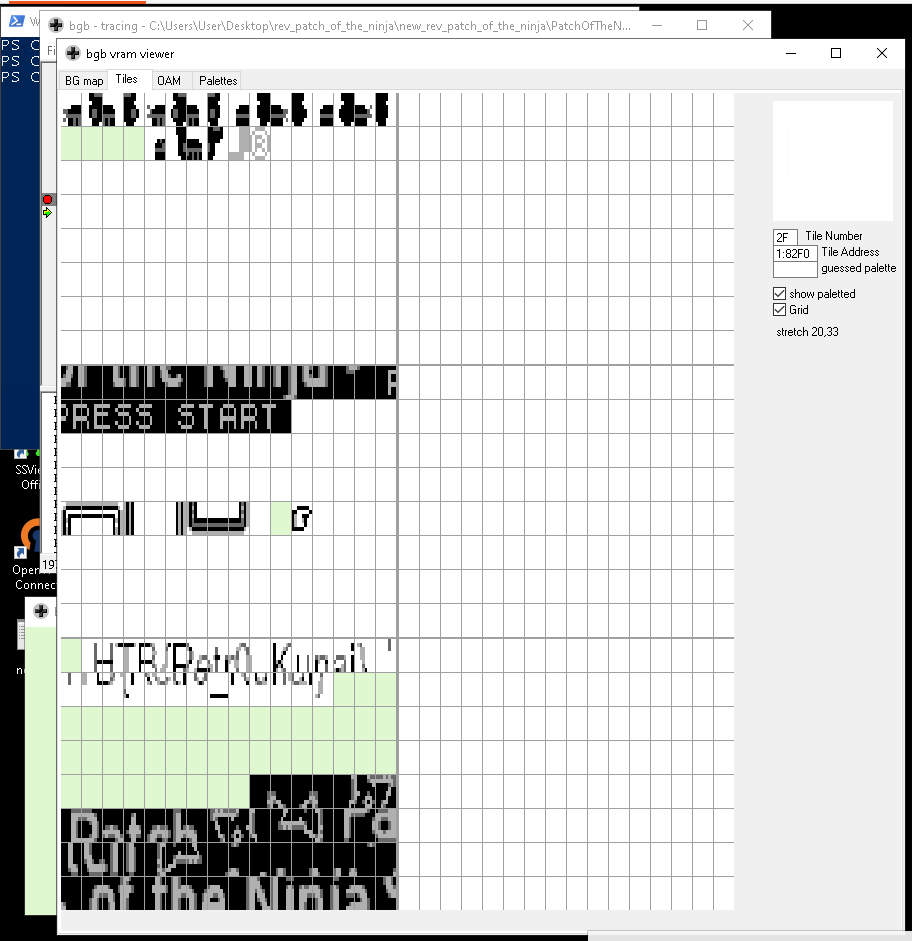
We explored some views like the tracing debugger and the vram viewer and were amazed. With these tools we started to investigate the boot process in order to find the source address of the main game logic.
We stepped to our mysterious reference and found commands that gHidra cant visualize. So we continued stepping over some functions.
Suddenly, at a moment when no one expected anything, new tiles were loaded into the vram. They were not just any tiles, instead the flag was now readable in the vram viewer.
Other resources
- https://github.com/Gekkio/GhidraBoy
- https://martinmelhus.com/squarectf-2017-writeup
- http://bgb.bircd.org/
Some useful resource
- https://wiki.ubuntuusers.de/VisualBoyAdvance/
- https://github.com/visualboyadvance-m/visualboyadvance-m
- https://github.com/LIJI32/SameBoy
- https://github.com/Gekkio/GhidraBoy/releases
- https://martinmelhus.com/squarectf-2017-writeup
- http://marc.rawer.de/Gameboy/Docs/GBCPUman.pdf
- https://www.megabeets.net/reverse-engineering-a-gameboy-rom-with-radare2/