We intercepted a serial communication between two microcontrollers. It seems that the first microcontroller is using a weird protocol to access a flash memory controlled by the second microcontroller. We were able to retrieve 16 sectors of the memory before the connection was disrupted. Can you retrieve what it was read?
Category: Hardware
Solver: davex
Writeup
For this challenge, the only thing you received was a zip file containing two files.
challenge.zip
sequence.logicdata
dump.bin
We looked up what kind of data we received. The dump.bin file seems like a memory dump and after researching the .logicdata type we found a free software called Saleae logic [1]. This program can capture logic sequence data and save them into .logicdata files. We downloaded the software and opened the sequence.logicdata file.
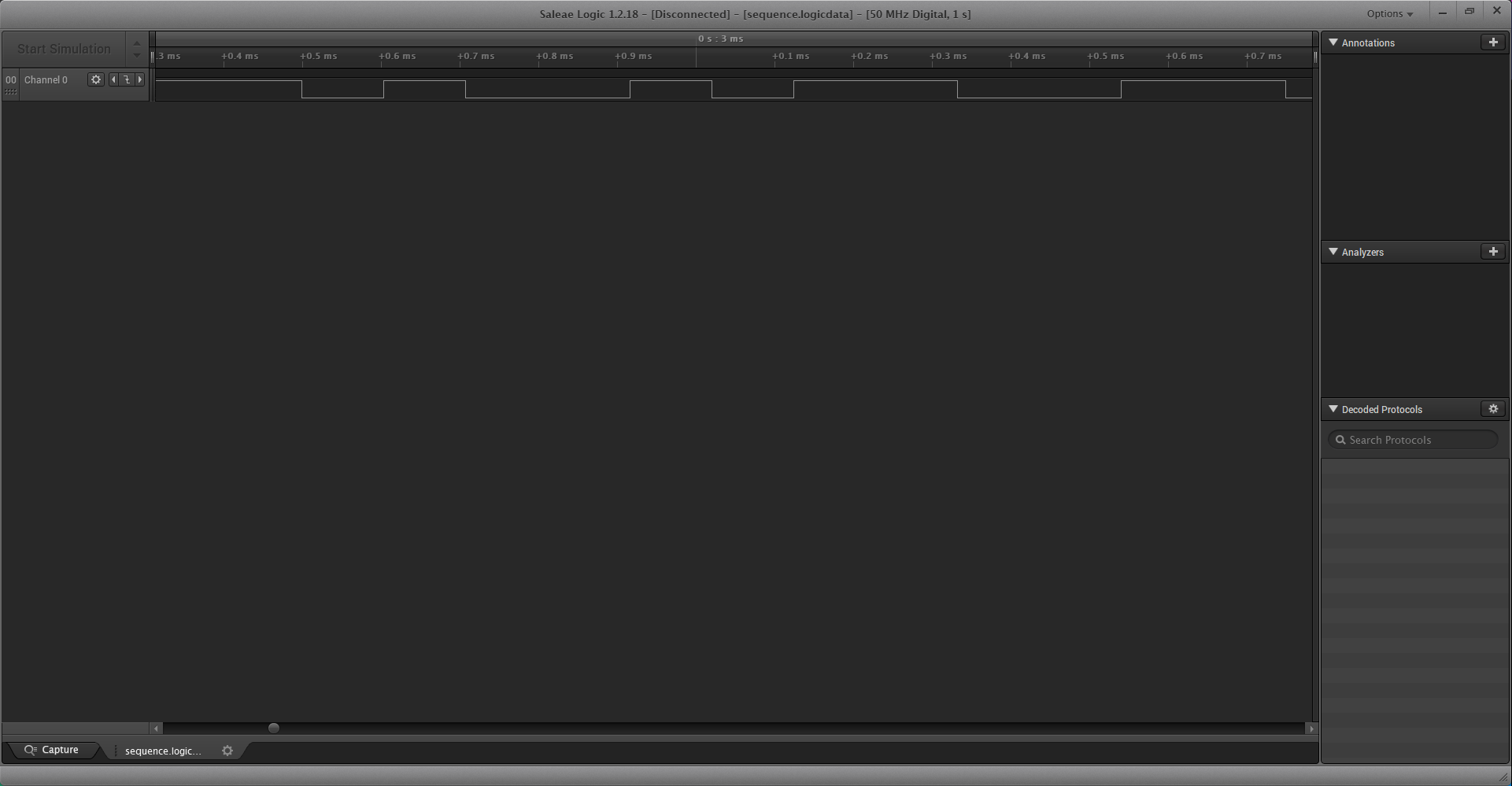
As you can see we can define analyzers for our sequence of data. We played around with these analyzers and found readable encoded data with the async serial analyzer. We did not find the same settings and some symbols got framing errors. Luckily those symbols also got encoded correctly and we received the following sequence out of the export. (We already cleaned up the export)
Init' 'W25Q128BV' 'SPI' 'Comm..xy' 'sector:xCOMMA' 'page:yCOMMA' 'page_offset:xy
14
17
27
11
04
15
19
40
21
51
18
06
49
02
31
50
28
41
32
35
24
39
42
36
45
03
43
20
00
01
09
44
38
07
22
08
13
23
37
10
47
05
33
26
46
25
We searched up the name W25Q128BV to see whats initialized here. We found documentation [2] of flash memory. This memory partitions the data into sectors with pages in it. With this information, the sequence data makes more sense because it looks like a memory query with the described parameters. This means that the first number of each row represents the x and the second number the y value of the request.
For example, the first row represents the query
x = 1
y = 4
sector: 1
page: 4
pageoffset: 14
We wrote a script to extract the queried data out of the memory dump dump.bin.
#!/usr/bin/env python3
import os
import sys
def main():
offsets = []
with open('./control.txt', 'r') as c:
lines = c.readlines()
for line in lines:
sector = int(line[0])
page = int(line[1])
offsets.append(sector * (16 * 256) + page * 256 + int(line))
the_flag = ""
with open('./dump.bin', 'rb') as f:
for offset in offsets:
f.seek(offset, 0)
the_flag += f.read(1).decode('utf-8')
print(the_flag)
if __name__ == '__main__':
main()
We dumped the number sequence into the control.txt file and let the script run and read the flag out of the memory
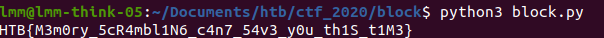
HTB{M3m0ry5cR4mbl1n6c4n754v3y0uth1St1M3}
Other resources
[1] https://www.saleae.com/downloads/
[2] https://www.winbond.com/resource-files/w25q128fv_revhh1_100913_website1.pdf