An unknown maintainer managed to push an update to one of our public docker images. Our SOC team reported suspicious traffic coming from some of our steam factories ever since. The update got retracted making us unable to investigate further. We are concerned that this might refer to a supply-chain attack. Could you investigate?
Docker Image: steammaintainer/gearrepairimage
Category: forensics
Solver: 3mb0
Flag: HTB{1_r34lly_l1k3_st34mpunk_r0b0ts!!!}
Writeup
Firstly, we download the provided docker image with docker pull steammaintainer/gearrepairimage and inspect the layers of it on DockerHub [1]:
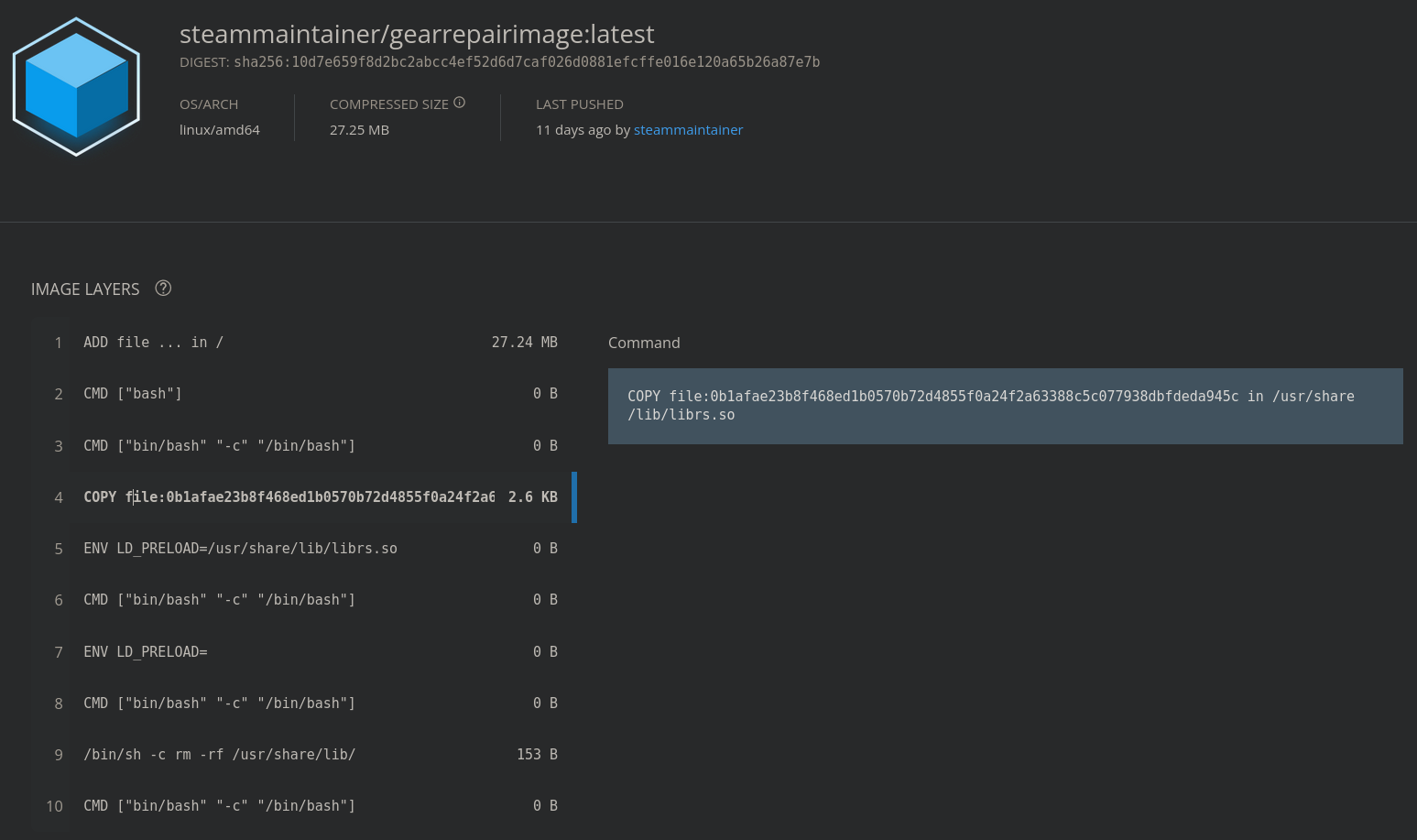
The file /usr/share/lib/librs.so was added and removed in previous layers. To get this file back, we search the layers in the local filesystem. Information about docker layers is saved in the subdirectories of /var/lib/docker/image/overlay2/layerdb/. Using the following bash script, we get the cache ID of all layers in the layer database and use it to look for the file /usr/share/lib/librs.so in the layer diff that is saved in the cache:
for directory in /var/lib/docker/image/overlay2/layerdb/sha256/*; do
cache_id=$(cat "$directory/cache-id")
echo "$directory: $cache_id$"
ls -lah "/var/lib/docker/overlay2/$cache_id/diff/usr/share/lib/librs.so"
done
This gives us the path to the file with its layer hash and cache ID:
/var/lib/docker/image/overlay2/layerdb/sha256/373b9aa2486847668a4827e9e45a21497ffbb2c7c0bdd3eb29c891b2f94b59e1: 2fef6fe4c4b2cb0a770160a643c743125c89b6b0ff1e8d8154cf9099666e15e6$
-rwxr-xr-x 1 root root 17K Nov 12 16:38 /var/lib/docker/overlay2/2fef6fe4c4b2cb0a770160a643c743125c89b6b0ff1e8d8154cf9099666e15e6/diff/usr/share/lib/librs.so
Using the file command, we find out that the extracted librs.so is an ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, BuildID[sha1]=b6e2da9852ab0b8f7aa409d6c5cf0f3c133b5ed7, not stripped
We then try to examine the file with Ghidra but have no success and remember that one should always try the simple things first. Using the strings command, we can easily extract the flag HTB{1_r34lly_l1k3_st34mpunk_r0b0ts!!!} from the binary:
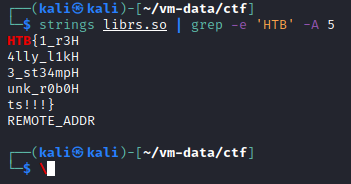
In hindsight, it would have been also easily possible to find the location of the binary using find because we were already aware of the exact name…
Other resources
[1] https://hub.docker.com/r/steammaintainer/gearrepairimage/tags